Security challenges are getting smarter day by day. Devices hardening, controlling the access and firewall features are all part of a secured network. But they cannot defend against fast moving virus and worms. A network should have the ability to identify and mitigate threats of virus and worms.
Intrusion Prevention Systems and Intrusion Detection Systems are required to identify and mitigate threats.In implementing IDS or IPS it is necessary to be familiar with the types of system available in placing of these systems, Host-Based and Network-Based Approaches.
IDS (Intrusion Detection Systems)
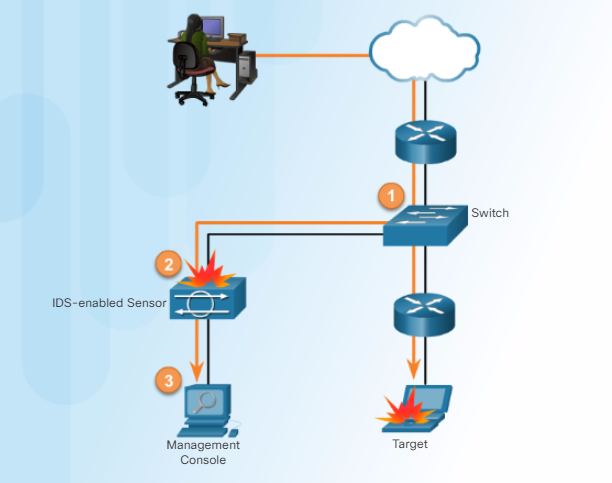
IDS are implemented to monitor the network traffic passively. This device copies and analyzes the network traffic rather than analyzing the actual packets and compare the packets with the known malware.
IDS works in offline mode.
- works passively
- physically positioned in a place where the traffic can be mirrored.
- unless the traffic is not mirrored then the traffic will not pass through the IDS.
The problem in IDS is it cannot prevent attacks and protect the network. It can only detect the attacks. The solution foe this is IPS.
IPS (Intrusion Prevention Systems)
IPS is built upon the technology of IDS. IDS monitors the traffic of layer 3 and layer 4. CISCO IPS platforms use several detection technologies.
- Signature based
- Profile based
- protocol analysis based
IPS can stops malicious packets from reaching the secured network by analyzing the actual packets and the negative side is it affects the packet flow of forwarded packets. If the IPS fails the the whole network goes down as it is configured in inline mode.


No comments:
Post a Comment